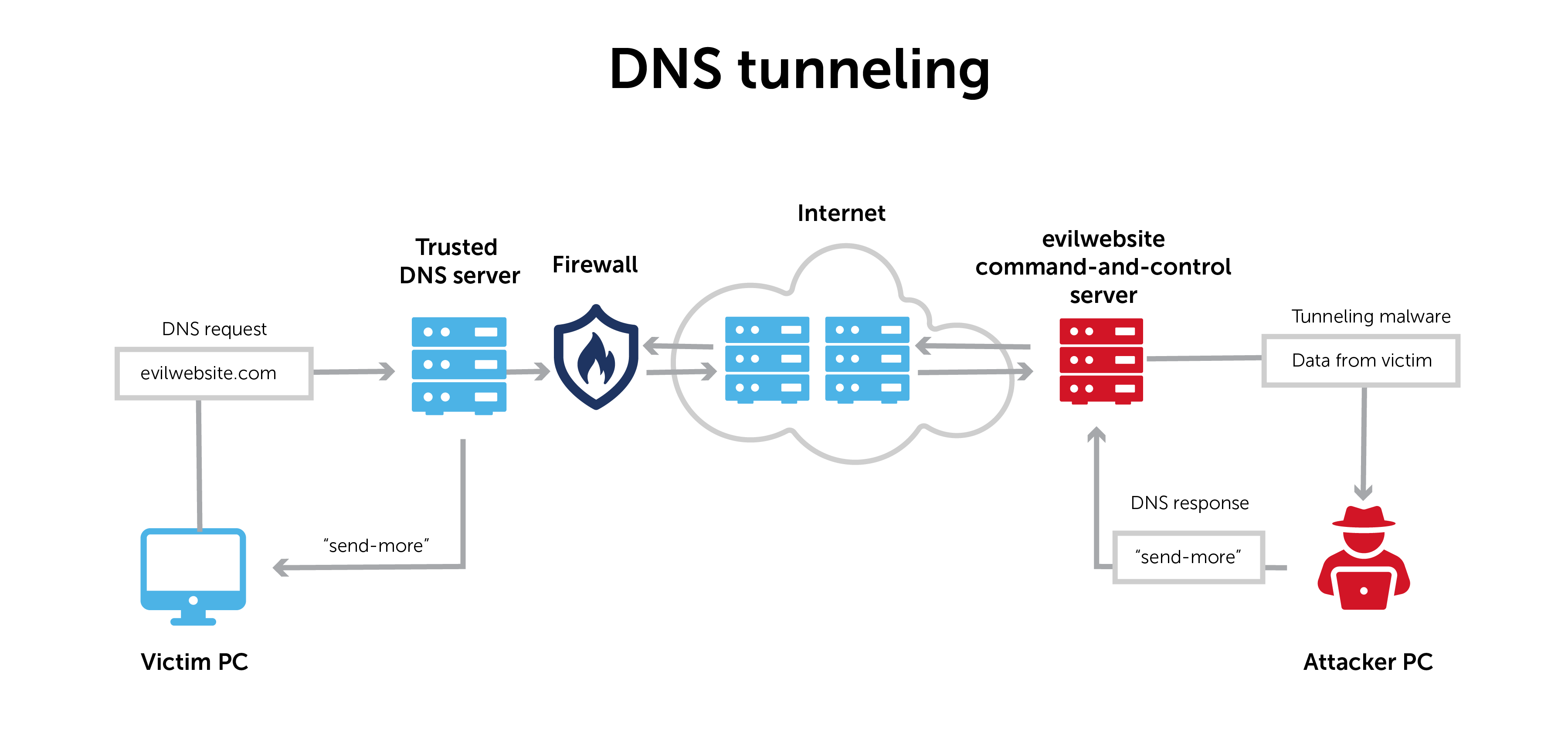
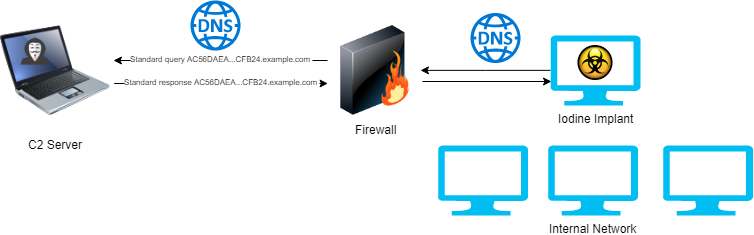
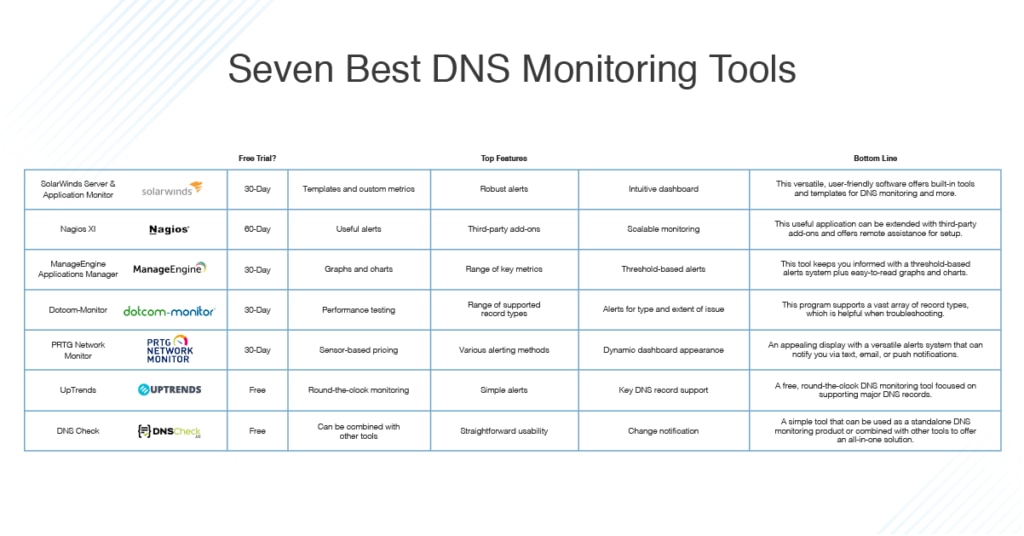
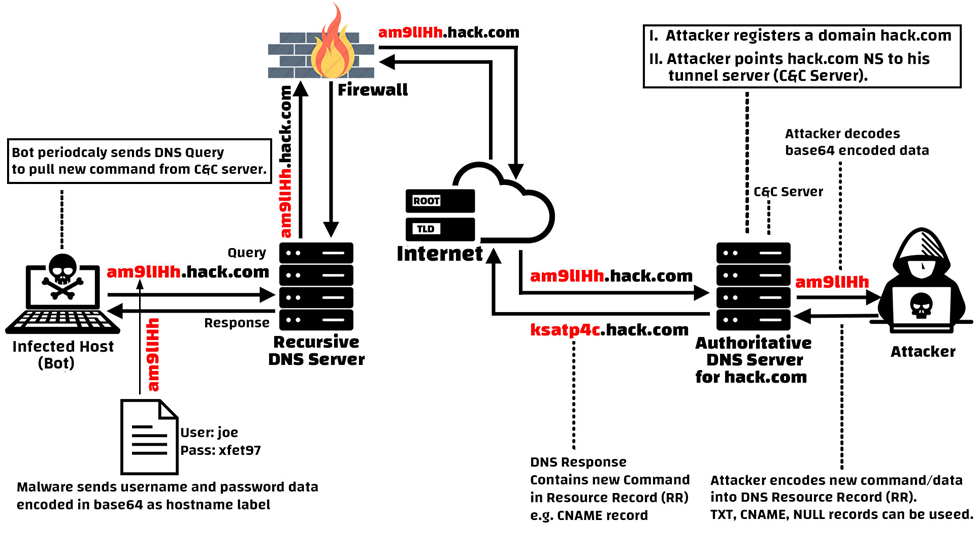
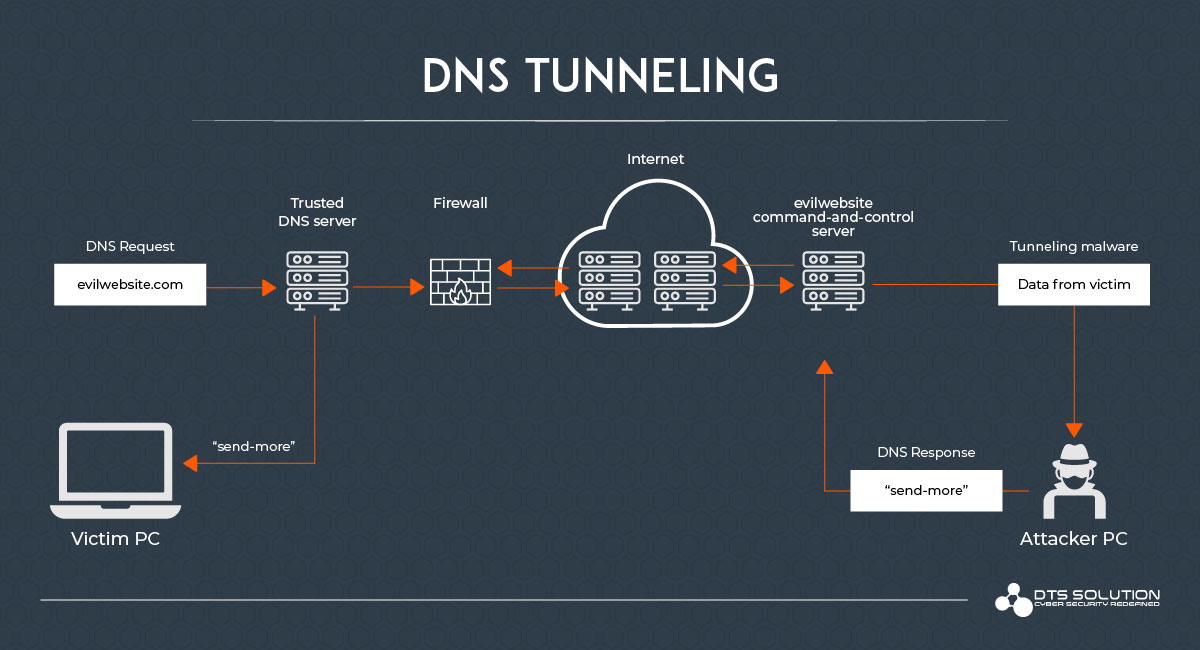
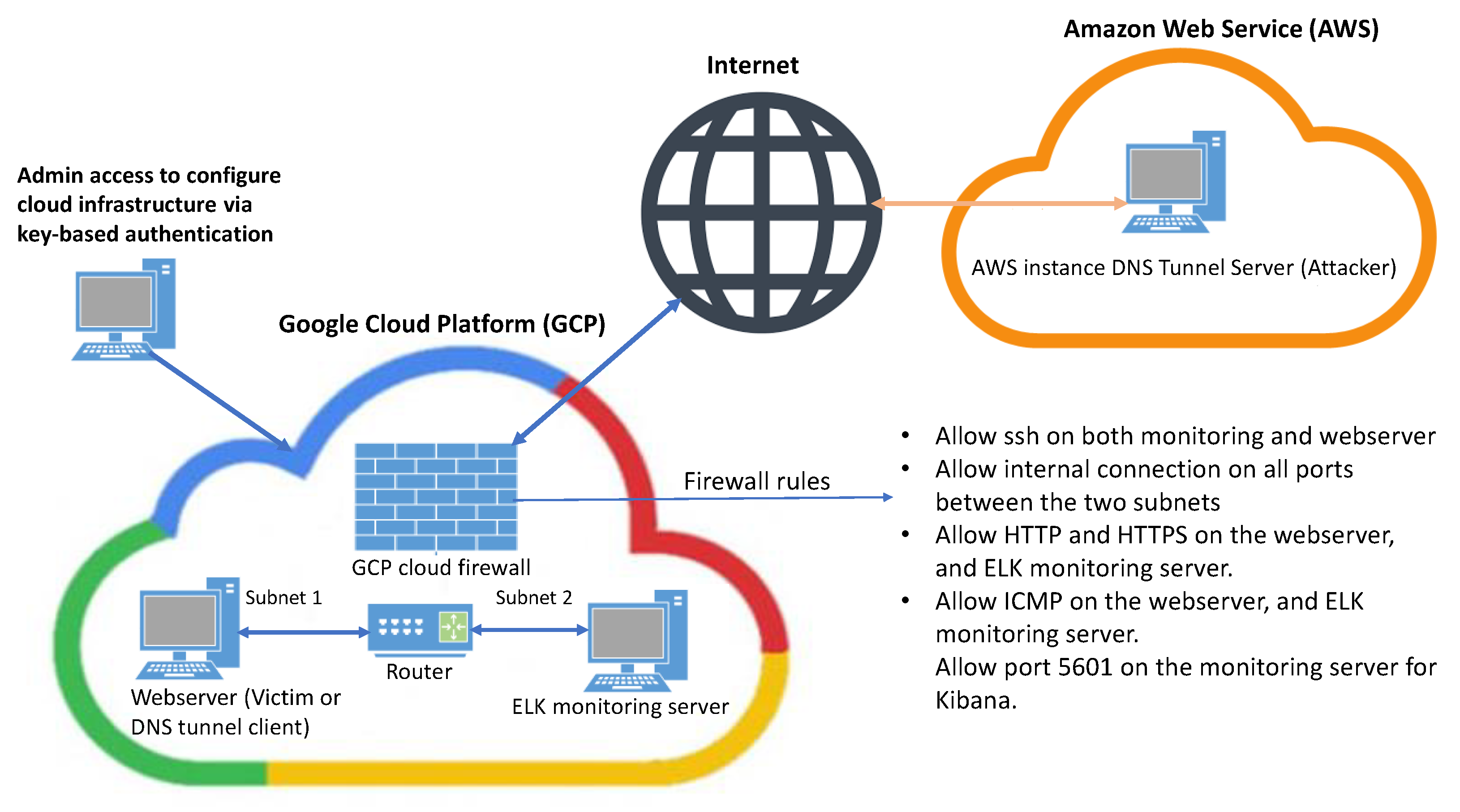
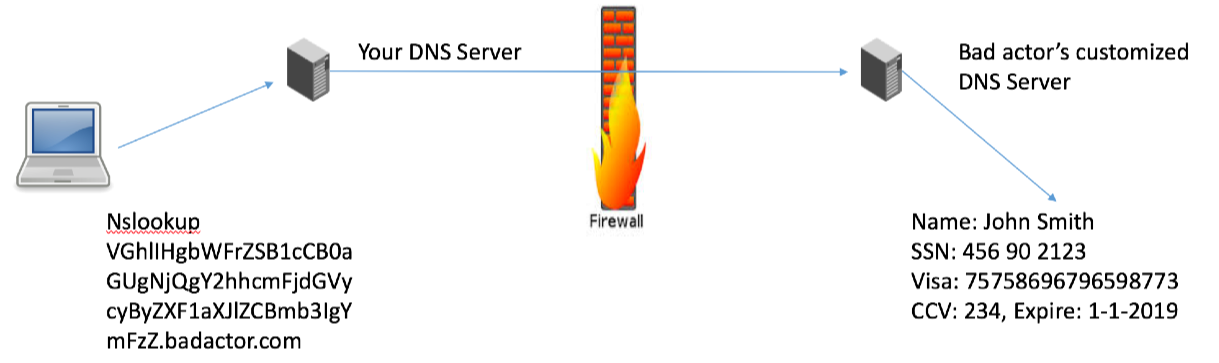
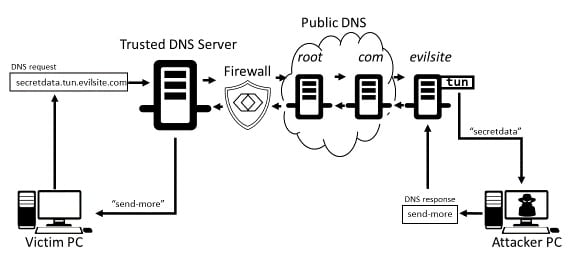
Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink

Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink